Author: Fatih Ermis | Senior Solution Consultant
Section 1: What is Cisco Cyber Vision?
The security layers used for IT have now become indispensable for OT security. Especially recently, most data leaks are made by infiltrating the inside through different means. It is seen that security products positioned for North-South internet traffic are not sufficient for such leaks. In addition to North-South traffic, similar data leaks can be prevented by routine anomaly/vulnerability scans on the East-West, i.e. horizontal axis.
Although most OT products work on intranet (closed circuit / closed to the internet) systems, information security gaps can occur at many points with different integrations. One of the biggest problems in OT technologies is visibility. One of the reasons for this is that there are too many devices in the structures and the structure is constantly being expanded uncontrollably by making additions. In addition, it can be added that a structure of this size cannot be intervened without any problems. Both the fact that critical services are running on it and that very serious financial losses can be experienced in the event of a problem can cause obstacles by the management in making the necessary improvements and/or security additions.
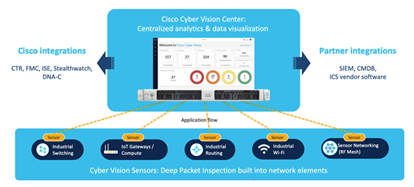
To prevent similar situations from occurring, Cisco aims to prevent such problems with its Cyber Vision product, which increases the visibility of OT environments, reveals existing threats, and creates existing inventories.

Cyber Vision to your institution;
- Providing full visibility for OT environments (assets and processes)
- Real-time monitoring of your dynamically changing inventory and network
( Dynamic Asset Management and Monitoring )
- Providing the same information security for the OT network as for IT,
- It will take your organization's security to the next level with comprehensive threat intelligence.
Security Assessments
Securing your OT infrastructure starts with a clear view of your asset inventory, communication models, and accurately positioned network maps (network topologies). Cyber Vision automatically generates a list of your industrial assets and detailed network maps.

Network Segmentation
Industrial security applications (best practices) recommend that networks be moved to compatible architectures, and in order to prevent a possible attack from spreading to the entire architecture, network segmentation and the ability to create policies between these segmented networks provide great benefits to institutions in terms of information security vulnerabilities. In this area, Cisco Cyber Vision product integrates with Cisco ISE (Identity Service Engine) to create asset groups and enables segmentation policies to be applied dynamically (dynamic network segmentation).
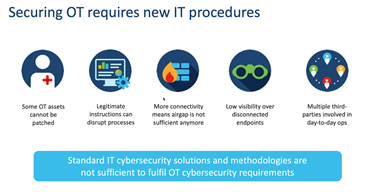
Standard IT cyber security solutions and methods may not always be sufficient to meet OT cyber security needs. In response to this need, Cisco has introduced its Cyber Vision product for the security of OT technologies.
Chapter 2: Cyber Vision Installation
To download Cyber Vision Center software;
https://software.cisco.com/download/home/286325414/type
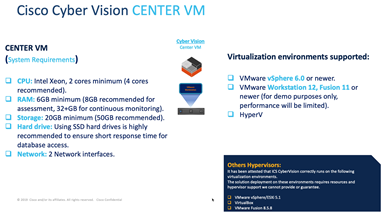
Features required for a virtual environment;
You can install and test Cyber Vision Center in a virtual environment with 2 CPUs, 6G RAM and 50GB HDD.
The installation steps are as follows;
- Cyber Vision software is downloaded from Cisco's website
- The downloaded .ova file is uploaded to the virtual environment.
- The installed virtual machine is opened and the system is started.
- Click “Start” to start the Cyber Vision Center installation.
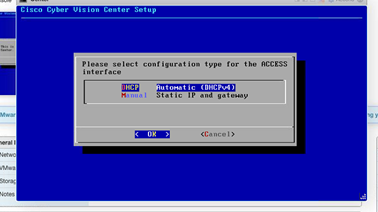
- Relevant DHCP settings are made.
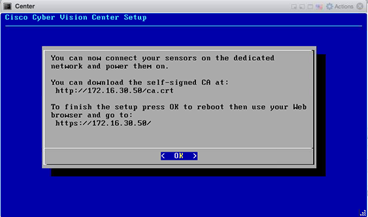
- Once the configuration is complete, the necessary information is entered into the Cyber Vision Center interface.
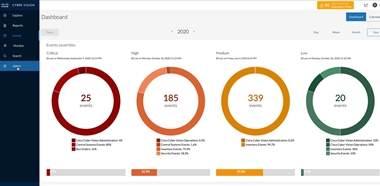
The Cyber Vision Center main screen is designed very simply and the Dashboard screen includes event levels with descriptions as critical, high, medium and low.
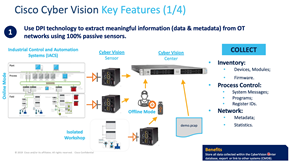
If we need to summarize Cyber Vision in 4 main features, we can summarize it as collecting all the information of the inventories by collecting meaningful information from your OT network via passive sensors using DPI technology; taking these inventories under control, generating an alarm when any possible opening/anomaly is detected and finally, providing comparative data for taking action by examining the records of past traffic movements.
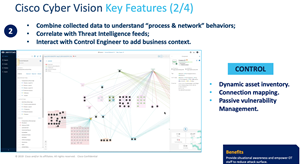
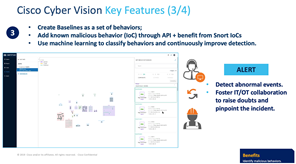

There are 2 options for Cyber Vision Licensing. Essential and Advantage licenses. In addition

As with many of Cisco's security products, a 90-day Essential or Advantage trial license is available.

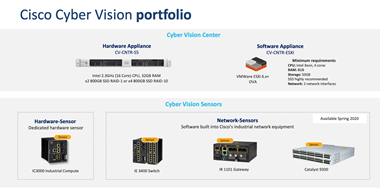
Cyber Vision consists of 2 main components, Cyber vision center (Hardware and Software) and Sensors. Cyber vision center can be installed in a virtual environment.
You can monitor security activities in your OT network from the Cyber Vision Center interface.
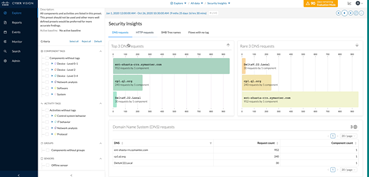
With the Network Explore feature, the map of which TAGGED or unTAGED devices are communicating with whom will increase the visibility of your network.
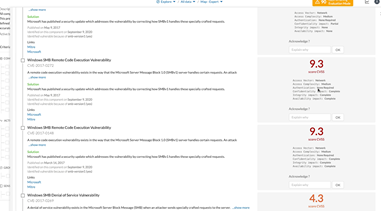
You can easily access reports on what type of vulnerabilities there are in your network, the score information, and the vulnerabilities that need to be closed.










